For my views on Internet piracy see my essay: Why Digital Piracy is Ethical and Necessary
We all know that you, as a law-abiding citizen, would never download a car. And yet there are people out there who download movies for free and refuse to add a few more bucks to the billions of dollars that movie studios squat upon. There are film executives who, thanks to cyber pirates, only have a net worth of $100 million instead of $101.
So how do they do it? How are these cyber criminals subverting our democracy and freedoms to acquire knowledge and entertainment for free without making the wealthy even wealthier? It all burns down to three simple letters: I2P.
I2P, or the Invisible Internet Project, is a project that enables anyone anywhere to download information in a way that makes it impossible for anyone to track them or reveal their identity. Many experts at the CNN agree that our democracy is in great danger when we freely allow citizens to practice speech that is genuinely free. Speech needs to be controlled and approved by the government, for our own security, and most importantly, the safety of our children. The cyber police work tirelessly to prevent free speech from actually taking place. But the pirates have found a home in I2P where no one can catch them.
I2P is slightly like TOR, which you may have heard of. However, unlike TOR, I2P is not used to browse normal internet sites (though it can be used that way), rather, it has its own sites, such as stats.i2p. And unlike TOR, I2P supports and encourages torrenting; it even has a built-in torrent client that is ready to go as soon as you install I2P.
Cyber pirates follow the following steps when they download high quality Blue Ray movies, ebook and textbook collections, and the latest Battlefield video game anonymously. We can show you the steps since downloading, installing and using I2P is perfectly legal under current laws (so long as you do not intentionally seek out and download copyrighted movies, books, songs, etc., see step 18 below for more clarification on this).
- First, they visit the I2P site to download the I2P software:
If the site is for some reason down or has moved, they can easily find the new site by Googling “download i2p”:
- Then they click the I2P download link to download the I2P software:
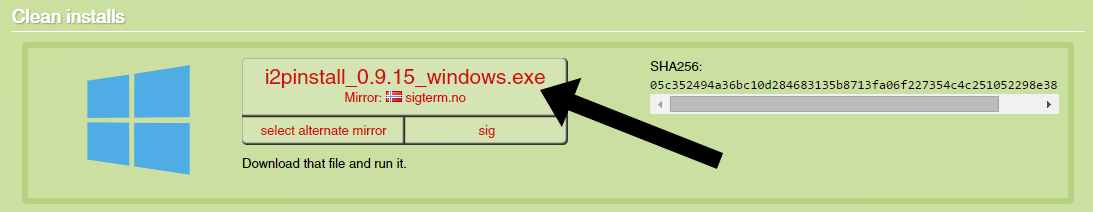
- Below is a picture of the finished I2P software download:
- They may then do a signature check to make sure their version of I2P has not been tampered with. You can read TOR’s guide for how to do this, and apply the same logic to I2P.
- Once I2P is installed, they do not run it. They will set up a browser to be fully dedicated to I2P. This means that the browser will be able to browse I2P websites, but not ordinary internet sites. In our example we show how the Opera browser can be configured to handle I2P. They click on the Opera button, then point to Settings->Preferences:
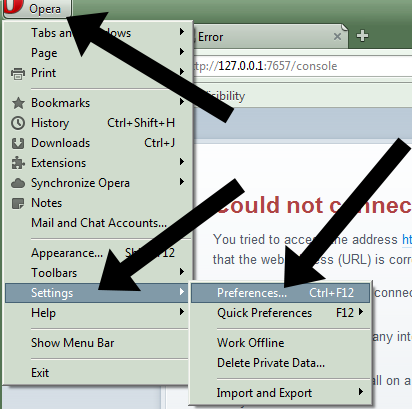
- Then they click the Advanced tab:
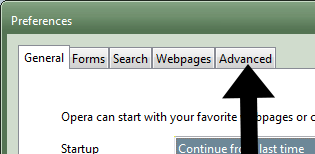
- Then they click on the Network section, then the “Proxy servers” button:

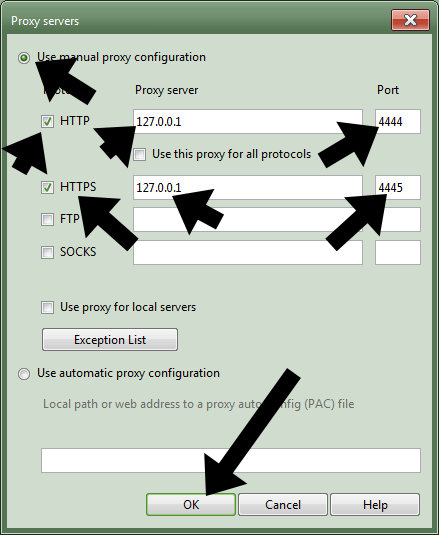
- Then they make the following changes to the window that pops up, then click “OK”:
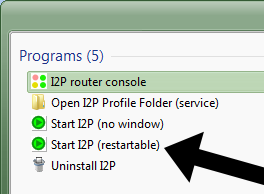
- Once they are done setting up Opera, they start I2P. There are two programs, and it doesn’t matter which one you run, the only difference is that the second one has a restart option. In our example we show you the restartable one:
- The I2P Service window shows up for them. Here they wait a little while for the program to fully start up.
- If all goes well, their computer launches their default browser, which could be Internet Explorer. While they do not want this, it is useful for getting the address to the I2P service. Thus they copy the address shown.
- They go to Opera and paste the address in the address bar. Then they drag the icon where it says “Web” to the bookmarks bar for easy navigation in the future.
- They wait a while as their I2P program becomes integrated into the worldwide network. They watch these two indicaters on the I2P homepage. Once they are green, they know they are good to go:
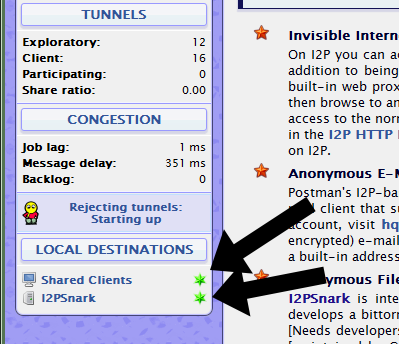
- Now, they click on the “Torrents” link at the top of the I2P Console.
- They are taken to I2PSnark, which is the built-in torrent client for I2P. Currently the client is empty since we haven’t added any torrents. They click on the “Postman” link to take them to the Postman tracker, which is the largest torrent tracker on I2P. There is also the Diftracker link, which is another tracker.
- Depending on how long the I2P program has been running, the Postman website will open immediately or after a while. They may also get a “Proxy server error” kind of page, which is nothing to be worried about, they will simply try the website again in 5-10 minutes.
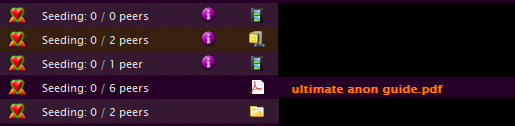
In the image it can be seen that the sneaky anonymous cyber pirates have uploaded torrents for a movie called Let the Right One In and a video game called Wasteland 2.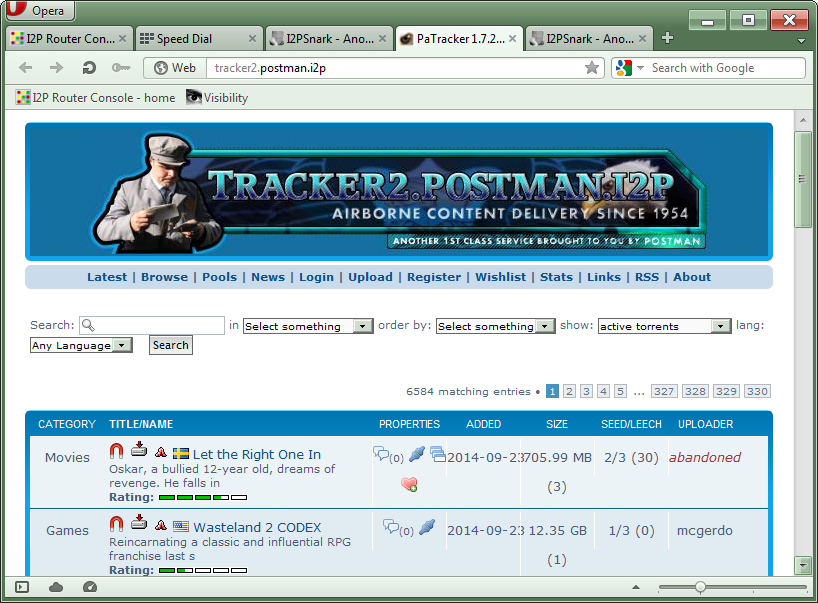
- Since we are perfectly law-abiding citizens, we will show an example of downloading a legal non-copyrighted file from the Postman I2P bittorrent tracker. But the pirates download movies and other files, committing copyrighted infringement. Of course, nobody, government or otherwise, can catch them do it, since everything is fully anonymous and encrypted. So they get away with downloading their favorite movies without making the super wealthy even wealthier. The communism!
Here, to find a legal file, we put the keyword “pdf” into the search box so that we only see ebook files, some of which are copyright-free and legally distributable.
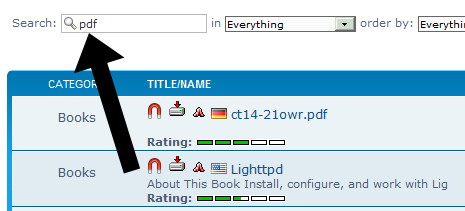
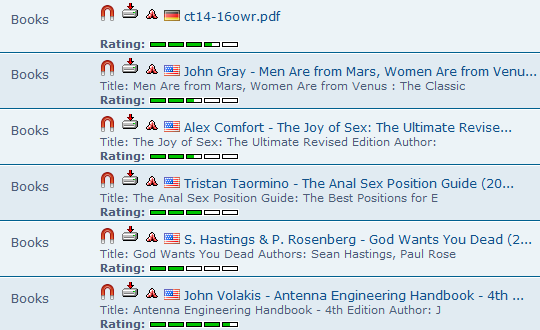
- Here is an example of some of the books that came up. We find some German magazine, a book by John Gray for clueless men trying to lead a politically correct life, two sex guides for autistic individuals, some convoluted self help nonsense, and a book for antenna nerds. These are all copyrighted books, therefore we will have to skip them; we wouldn’t download a car, so why would we download books? Of course, balaclava-wearing cyber pirates do not skip them just because they are copyrighted, since they know the cyber police have no way of catching them, since they are using I2P.
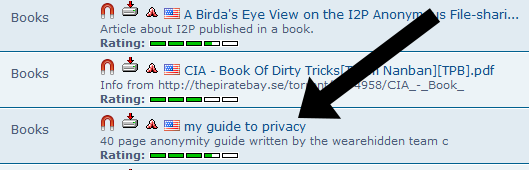
- After a very, very long time, we find a book that seems copyright-free.
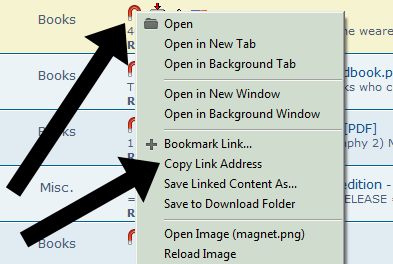
- Here, the pirates will right-click the magnet icon on the left of the book title and click “Copy Link Address”.
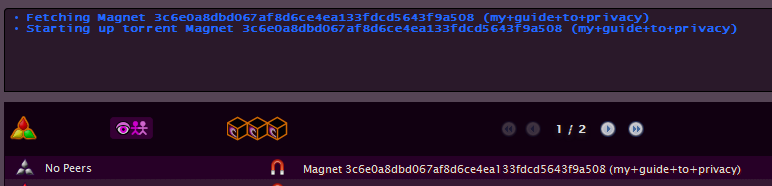
- Then, they will go back to I2PSnark, paste the link in the “From URL” box, then click “Add torrent”.

- Below we see that the torrent has been added to the list of torrents. The word “Magnet” ahead of all those numbers tells the pirate that the torrent file hasn’t been fetched yet (it usually takes a minute or two). Once it is, the name for the torrent will be shown.
- Below you can see the finished torrent being seeded. We have blacked out the names of the other torrents for undisclosed reasons. Seeding is also perfectly anonymous; therefore pirates often leave many torrents running in the seeding mode to help other pirates download things faster. Due to all of the cryptography that happens, downloading more than 5 torrents at the same time can cause significant CPU usage.